Every campus has unique security needs shaped by its layout, community, and daily operations. While traditional security measures often take a one-size-fits-all approach, VOLT AI's customizable rules engine allows you to create a tailored security strategy that proactively addresses your specific challenges.
By leveraging your existing camera infrastructure with intelligent rules, you can transform from reactive to proactive security management.
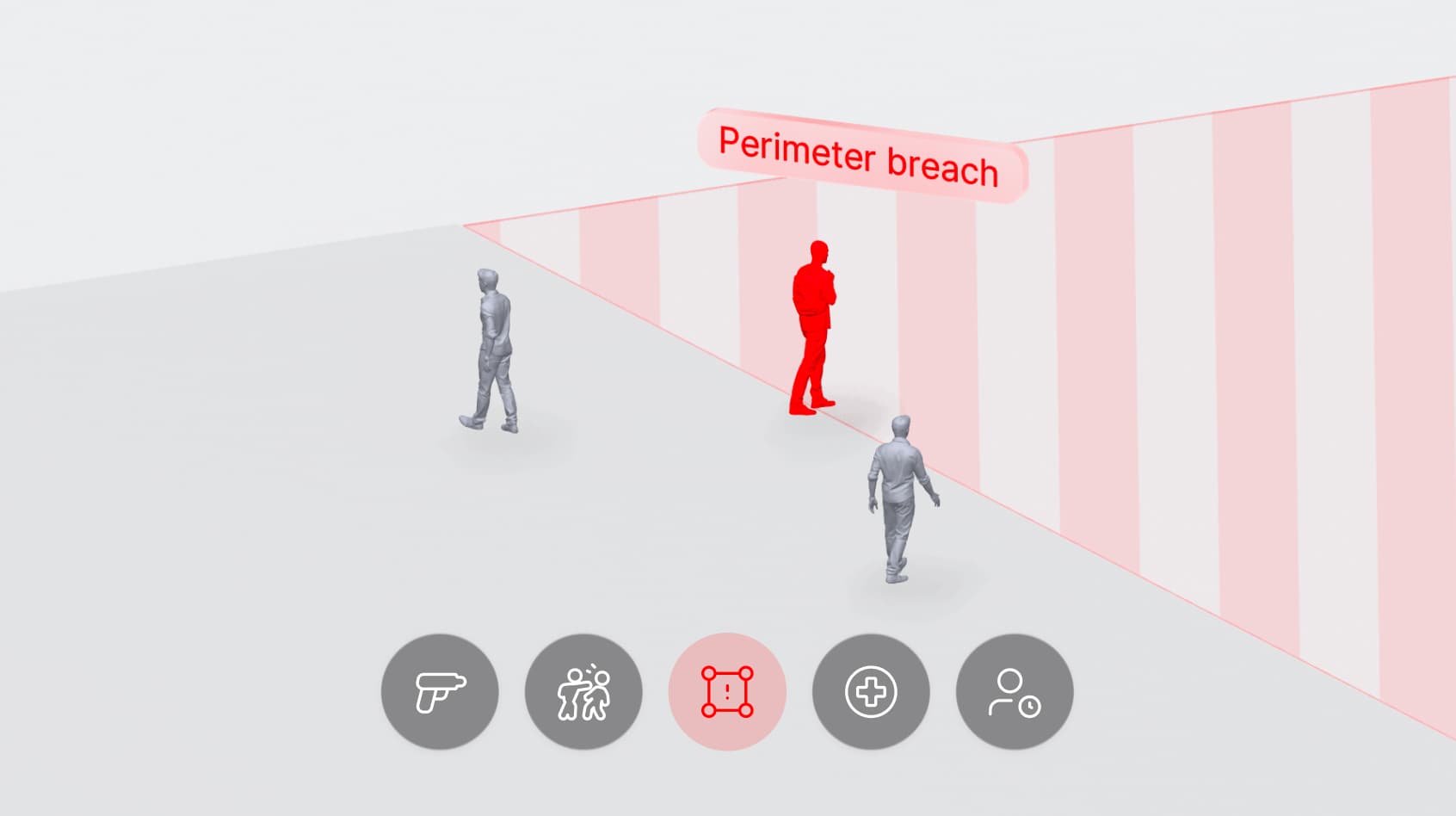
The Foundation: Understanding Rule Types
The VOLT AI system offers two fundamental types of rules that work together to create comprehensive security coverage. Facility-wide rules serve as your primary security foundation, providing essential monitoring across your entire campus.
These typically include weapon detection, person down alerts, and fight detection - critical safety measures that need to operate continuously throughout your entire facility.
Zone-specific rules complement this foundation by allowing precise control over distinct areas.Typically these types of rules include trigger off of a: person or vehicle loitering, person present, or moving vehicle. These rules can account for the unique characteristics and requirements of different spaces within your facility. For example, a parking area might need different monitoring parameters than a building entrance or a restricted storage area.
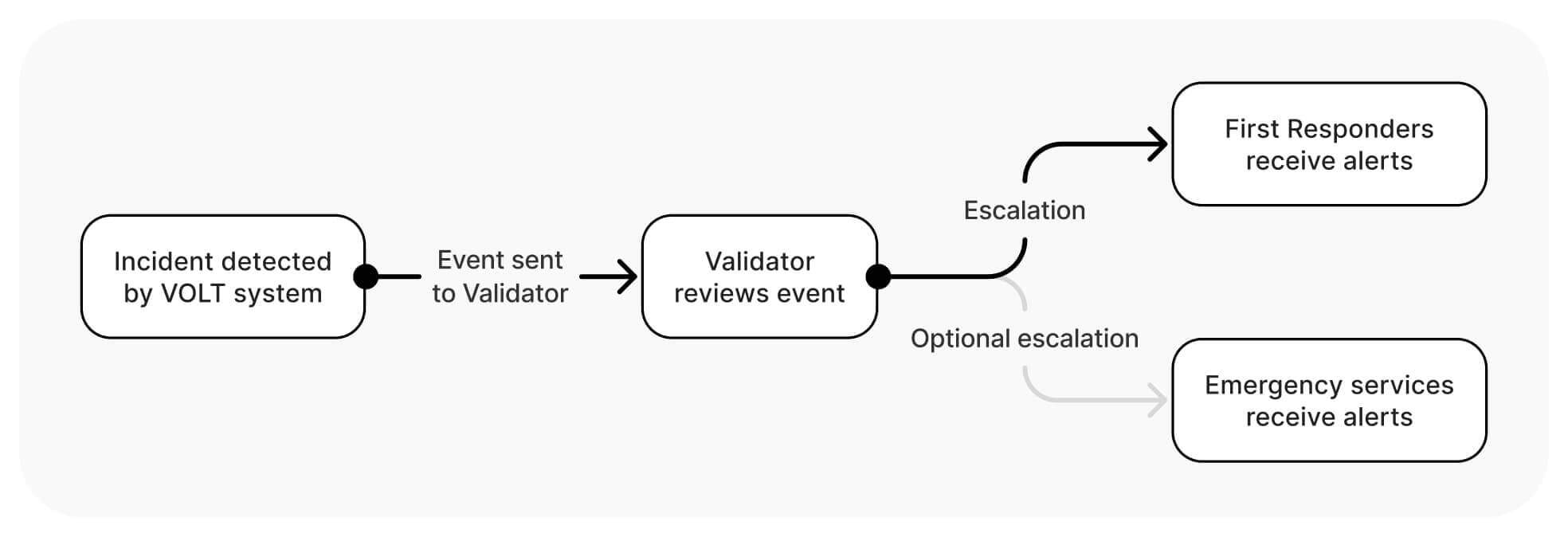
Building Your Strategic Framework
When implementing your rule strategy, timing becomes a crucial consideration. Many facilities find that different times of day require different security approaches. A building entrance might need strict occupancy monitoring during business hours but ensuring no people are detected after hours. Similarly, loitering detection thresholds might vary between day time and after dark.
Location-based customization forms another vital component of your strategy. Each area of your facility likely has distinct security needs and challenges. Parking areas might benefit from people loitering detection and extended dwell time monitoring at payment kiosks.
High-value areas could require object left behind detection combined with strict access monitoring. Entry points often need a combination of weapons detection and person loitering, crowd forming, or person detected (outside of business hours).
Alert escalation protocols complete your framework by ensuring the right people receive notifications at the right time. Critical incidents like weapon detection or medical emergencies can trigger immediate alerts to security teams and administrators, while more routine notifications might route to facility management.
These escalation chains can adapt based on the time of day or the specific type of incident detected.
Example Rules and Real-World Applications from VOLT AI Customers
The power of custom rules becomes evident in real-world applications. One university faced ongoing bike theft issues at specific rack locations. By implementing targeted loitering detection with custom dwell time thresholds, they significantly reduced theft incidents.
Medical emergency response provides another compelling example. A school implemented person down detection across their campus, leading to a dramatic improvement in response times.
In one instance, the system detected a student having a medical emergency in an empty hallway, enabling a nurse to respond within 15 seconds. Without this detection capability, the student might have gone unnoticed for a dangerous amount of time.
Review this list of examples from our real-world customers.
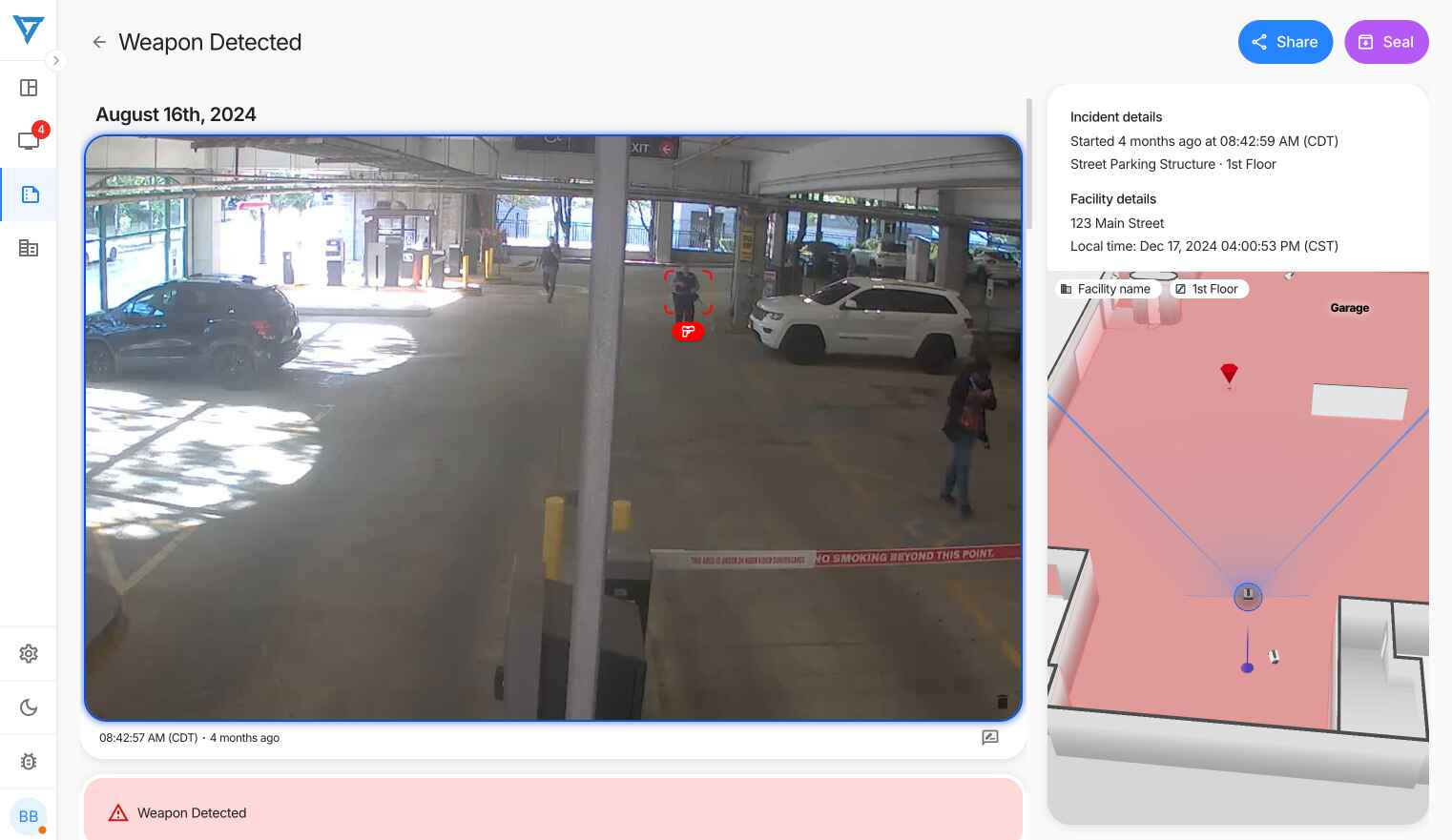
VOLT AI's weapon detection capability extends beyond simple identification, proving effective at detecting firearms and tracking their presence even after it has been put away. The system demonstrates its precision by successfully identifying training equipment like ROTC rifles and color guard equipment while maintaining vigilance for actual threats. One school administrator reported receiving weapon alerts before individuals even reached building entrances, providing crucial response time. Organizations can customize their notification protocols, choosing between automatic law enforcement notification or routing through internal security teams first.
Medical Emergency Detection
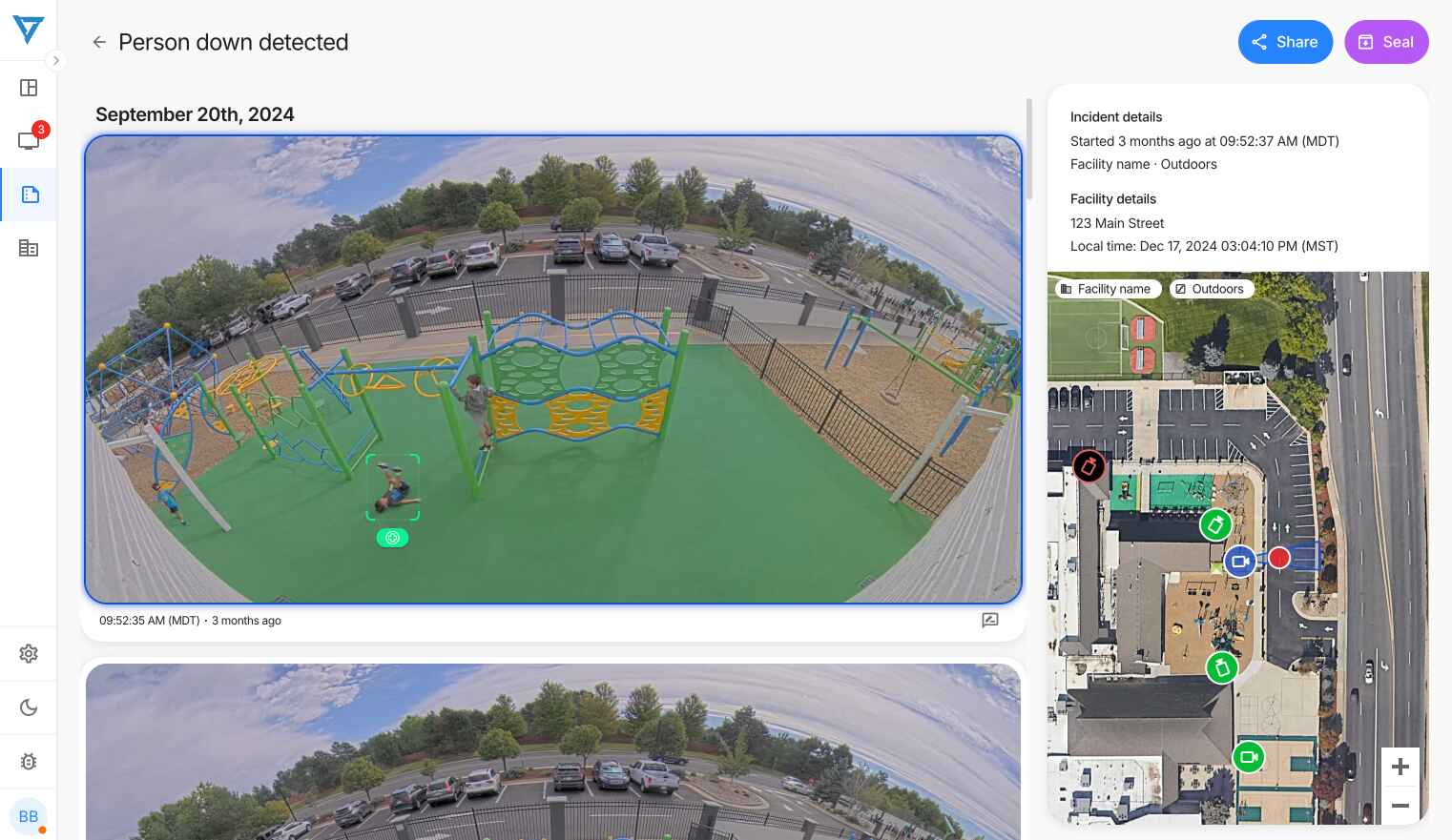
At another facility, the system identified a person who had fallen in an elevator lobby while others walked past. The technology recognizes individuals on the ground or in distress, particularly valuable in areas with limited staff presence or visibility. This capability has transformed emergency response times, especially during off-hours or in less-trafficked areas.
Fight Detection
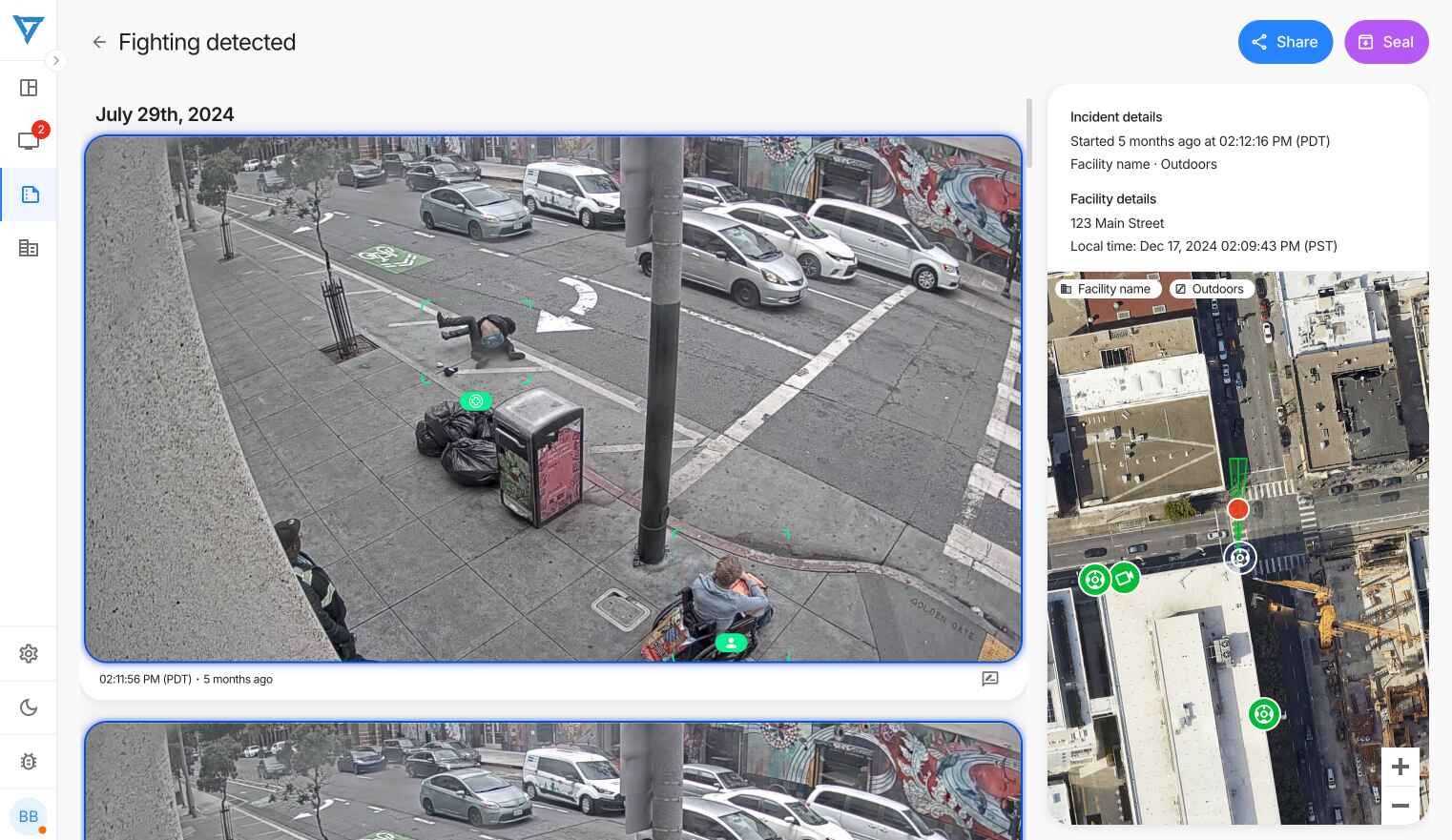
Fight detection capabilities have demonstrated remarkable accuracy in identifying various types of physical altercations. The system successfully distinguishes between casual horseplay and actual fights, while also detecting pre-planned confrontations like "slap boxing" matches. When fights are detected, security teams typically achieve response times within 20-30 seconds, allowing for rapid intervention before situations escalate. This proactive detection has proven particularly valuable in school environments where early intervention is crucial.
Crowd Formation Rules
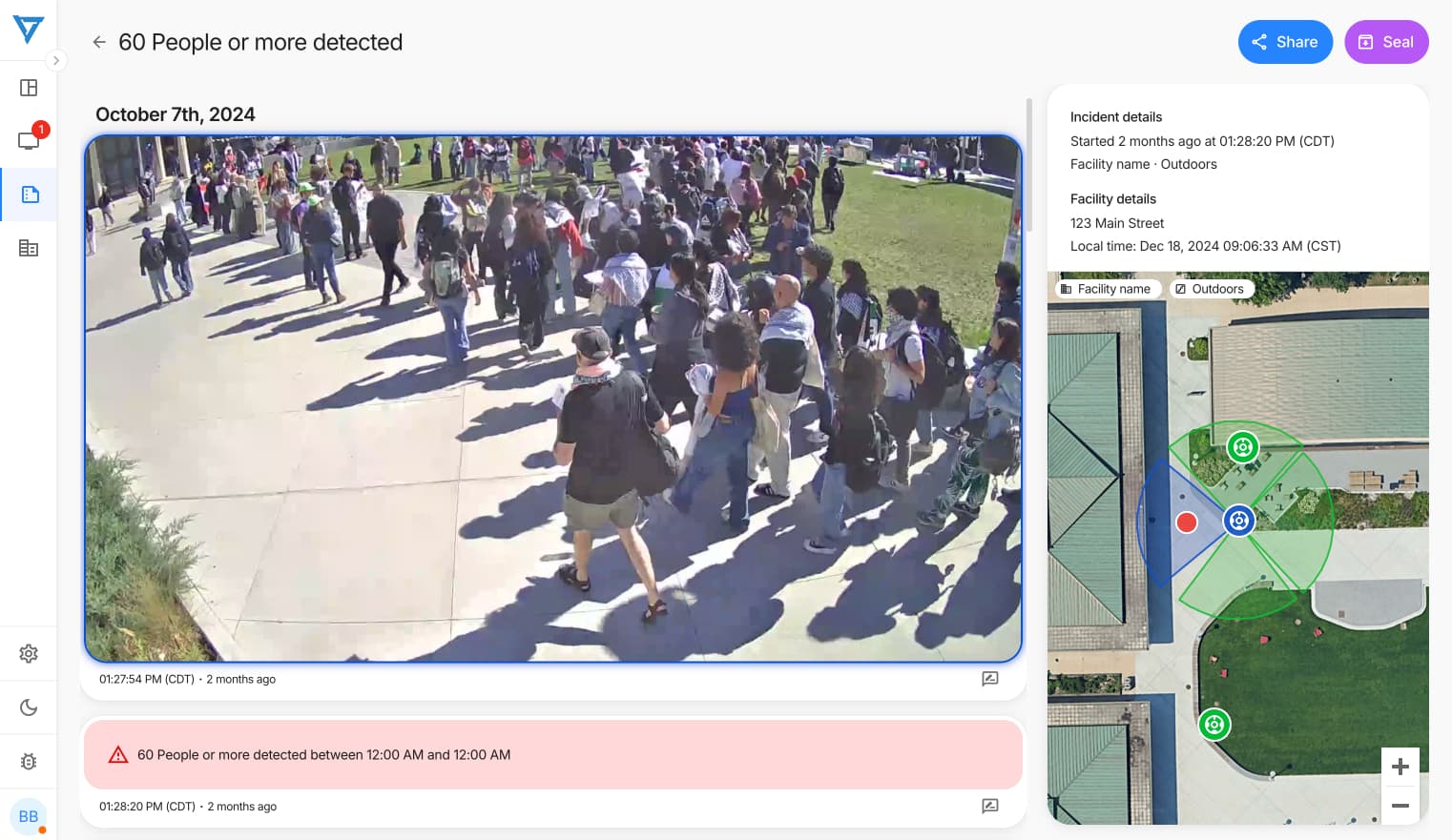
Crowd detection rules can be finely tuned to match facility needs and normal traffic patterns. Organizations commonly set facility-wide alerts for gatherings of 15 or more people, while creating zone-specific thresholds for different areas. For example, one facility sets different crowd limits for their pool area - allowing larger groups during business hours but triggering alerts for smaller gatherings after hours. This capability helps security teams identify potential conflicts before they escalate by recognizing unusual crowd formations.
Loitering Detection
Loitering detection has proven especially valuable in preventing theft and unauthorized access. Facilities can set time-based monitoring near vulnerable areas like bike racks and scooter parking, with custom thresholds for different locations.
Some organizations implement creative solutions, such as masking areas where gathering is normal (like benches or walls) while maintaining vigilance in more sensitive zones. After-hours monitoring can use different time thresholds, adapting to changed risk profiles during closed hours.
Access Control Rules
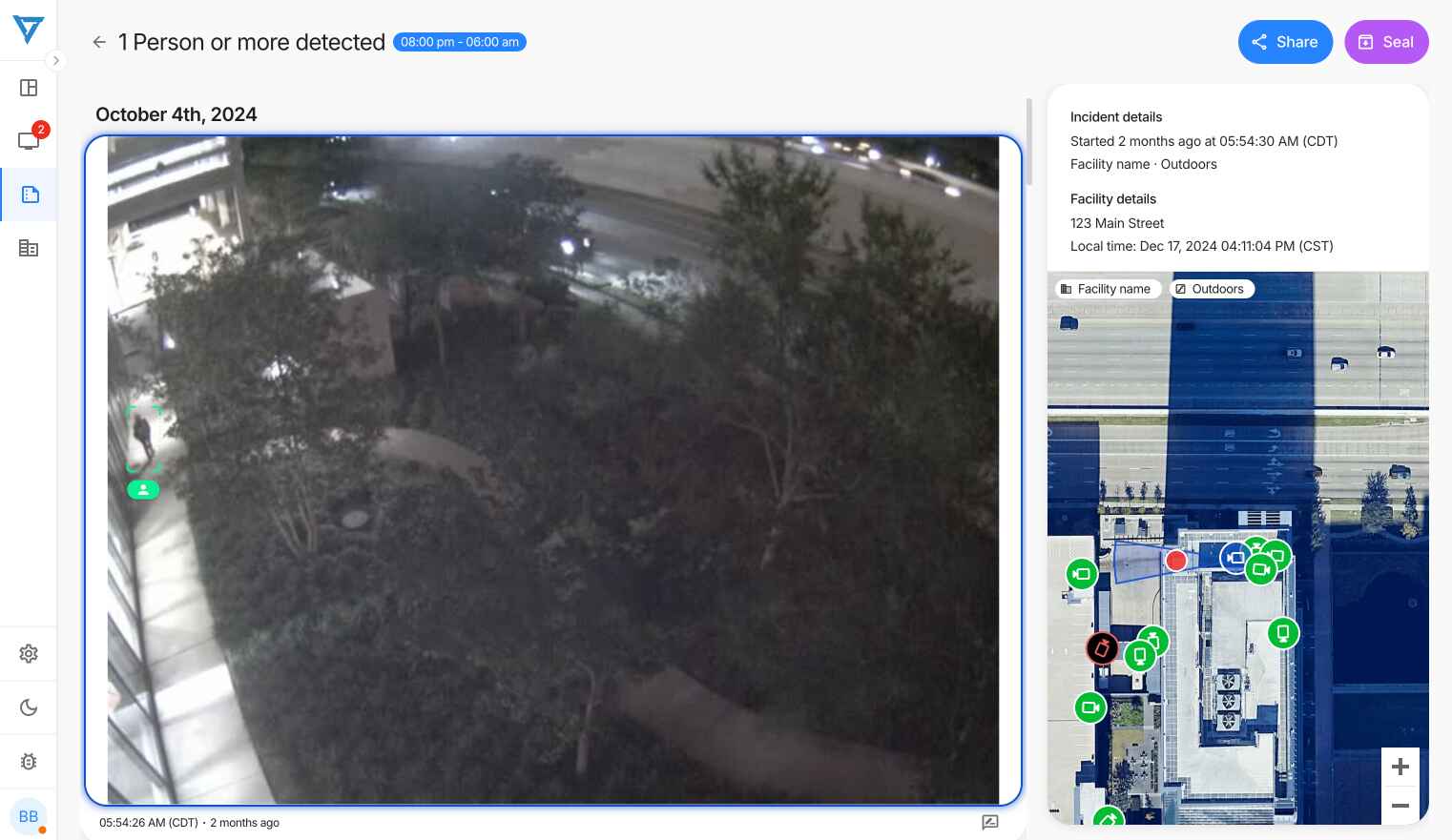
Access control monitoring combines multiple rule types to create comprehensive security coverage. Monitoring to ensure no people are present during closed hours helps identify any unauthorized presence, while movement tracking in restricted areas provides detailed awareness of activity patterns.
;Vehicle-Related Rules
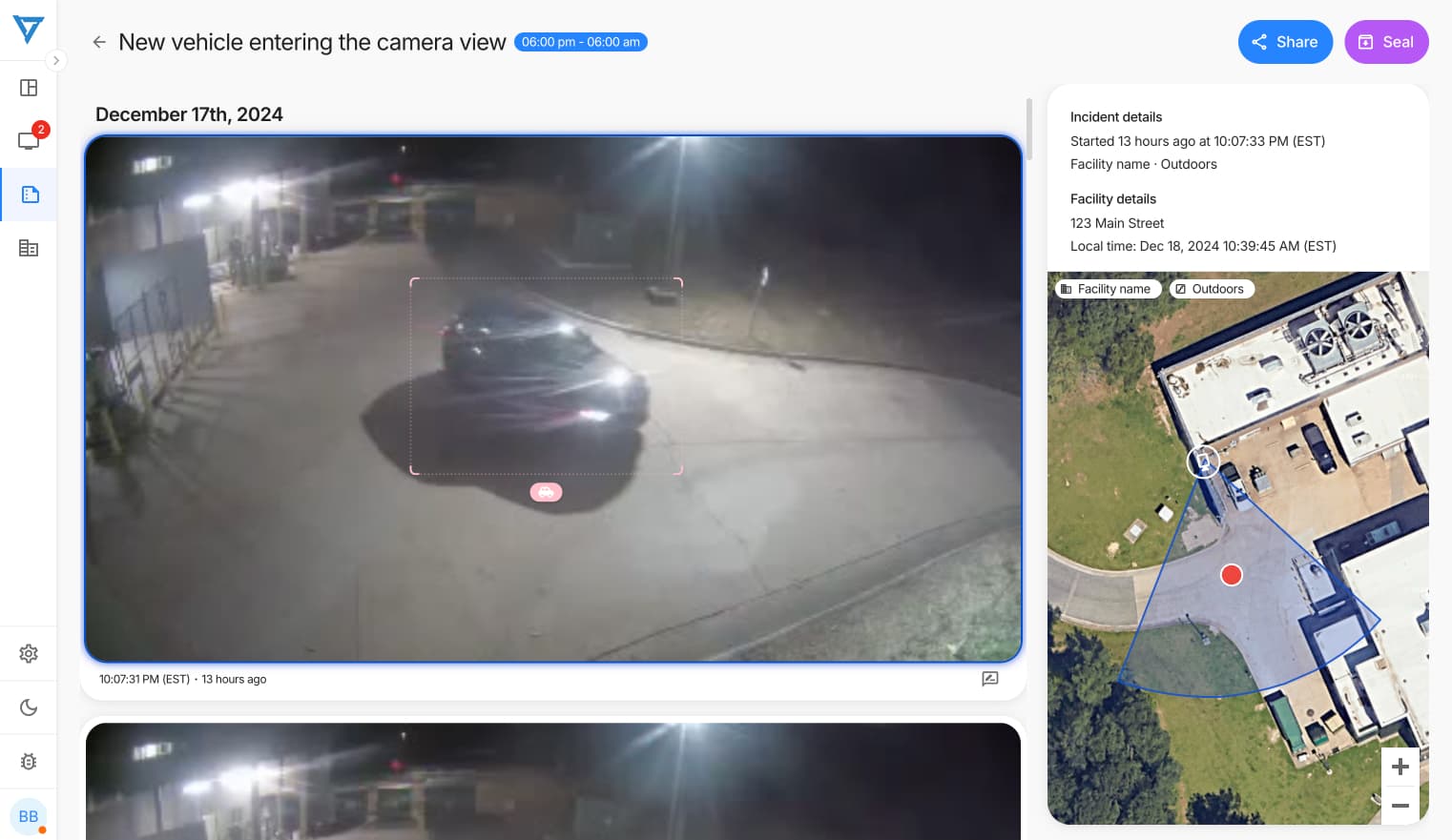
Vehicle monitoring rules address multiple security concerns, from preventing vandalism to detecting suspicious behavior. Extended dwell time monitoring at parking payment kiosks helps prevent damage to equipment, while moving vehicle detection during restricted hours identifies unauthorized access.
The system can monitor parking gate areas for potential vandalism attempts and track vehicle loitering in sensitive areas. These capabilities have helped numerous facilities reduce property damage and theft incidents.
Time-Based Rule Implementation
Time-based rules allow facilities to adapt their security posture throughout the day. For example, a pool area might allow larger groups during regular hours but trigger alerts for smaller gatherings after closing.
Some facilities implement rules during overnight hours to ensure nobody is present while maintaining different thresholds during business hours. This flexible approach allows organizations to maintain appropriate security levels while accommodating normal facility usage patterns.
Theft Prevention Rules
One urban university campus faced frequent bike and scooter thefts, particularly around campus entry points. Their security team implemented a sophisticated combination of rules that transformed their response to these incidents.
They created a masking zone for the seating wall near the racks where students normally gathered, while maintaining a shorter two-minute loitering alert for the rack area itself. Additionally, they implemented rules to ensure no people were present in these areas during overnight hours, successfully preventing after-hours theft attempts. The result was a significant reduction in bike theft incidents and improved recovery rates when thefts occurred.
This example demonstrates how rules can be refined based on real incidents and evolving theft techniques. By combining loitering detection, zone masking, time-based occupancy rules, and customized alert thresholds, the university created an effective theft prevention strategy that addressed its specific challenges.
They also discovered that implementing stringent monitoring rules around high-value storage areas helped catch perpetrators during the attempt phase, rather than investigating after items went missing. This proactive approach has become a model for other campuses facing similar challenges.
They also discovered that implementing stringent monitoring rules around high-value storage areas helped catch perpetrators during the attempt phase, rather than investigating after items went missing. This proactive approach has become a model for other campuses facing similar challenges.
Location-Specific Applications
Different areas of a facility often require unique security approaches. Parking facilities might combine extended dwell time monitoring at payment kiosks with gate arm vandalism prevention and after-hours vehicle movement detection.
High-traffic areas might use different crowd thresholds during various times of day, while restricted areas maintain stricter access controls. This zone-based approach allows organizations to create security protocols tailored to each area's specific risks and operational requirements.
Organizations typically find the most success by starting with broader facility-wide rules before adding zone-specific customizations. Regular review and adjustment of thresholds helps optimize system performance, while customized escalation protocols ensure appropriate response to different types of alerts. The key is finding the right balance between robust security coverage and operational efficiency, adapting rules as needs change and new patterns emerge.
Optimizing Your Rule Configuration
Rule optimization is an ongoing process that requires regular assessment and refinement. Many organizations find success by starting with broader facility-wide rules and then adjusting based on actual usage patterns and alert volumes. This approach allows you to establish baseline security while gathering data about your specific needs and challenges.
Regular review sessions with the VOLT team help ensure your rules continue to meet your evolving security requirements. Quarterly assessments of rule effectiveness, combined with analysis of false positive rates, allow you to fine-tune your configuration for optimal performance. As your facility's usage patterns change or new security challenges emerge, your rule set can adapt accordingly.
The Partnership Approach
VOLT AI believes in partnering with our customers throughout their security journey. Our team works closely with you during initial setup to establish effective baseline rules that address your immediate security needs. Regular check-ins help optimize performance and ensure your rule configuration continues to evolve with your requirements.
This collaborative approach extends beyond just technical setup. We share insights from successful implementations across various facilities, helping you benefit from proven security strategies while maintaining your unique security profile. Our goal is to help you create a security framework that's both robust and adaptable to your changing needs.
Remember, transforming your security approach from reactive to proactive doesn't happen overnight. It's an iterative process that requires attention to your facility's specific challenges and careful consideration of how different rules can work together to create comprehensive protection. With the right strategy and ongoing optimization, your custom rules can significantly enhance your security operations while reducing the burden on your team.
Contact your VOLT AI representative to schedule a rule optimization session and take the next step in enhancing your security strategy.


